What challenges will the IoT security in 2017 face?
At present, the Internet of Things is the main force of weaponized DDoS. In 2016, the Internet of Things botnet was exploited to launch a number of attacks, including unprecedented large-scale DDoS attacks. The Internet of Things will continue to play this role in the next few years. Tools to implement such attacks are publicly available for free. It is estimated that by 2020, IoT equipment will reach 20 billion units. Therefore, from now on, more malicious attackers will implement more frequent and destructive attacks. Every business or organization must protect itself from such potential DDoS attacks. With the continuous development of the Internet of Things, new threats will be faced in 2017, and organizations and consumers must have effective defense. The following are the possible IoT threats in 2017 and the measures that organizations can protect themselves. Internet of Things ransom attack In 2017, from cars to medical devices, hackers will use ransom attacks more and more as more machines and sensors are available. Who will not pay the ransom to re-use the home thermostat or adjust the heartbeat pacemaker? While IoT devices can be a target for threats, they can also be perpetrators. With publicly available hacking tools, DDoS ransomware attacks can take advantage of "thingbots", large-scale systems of hijacked devices. These things often share IP addresses and unusual operating systems and are relatively difficult to identify. Although the Internet of Things ransom attack is different from conventional ransomware, the rules are the same: paying ransom often leads to long-term or repeated attacks. If you take a strong security posture and make your business a difficult goal, there will be fewer concerns. The Internet of Things becomes the ultimate endpoint, and it will fall into an uncontrollable state within a few years. The IoT threat was hit hard in 2016, hitting the largest DDoS attack ever, and a botnet of 25,000 camcorders and CCTV cameras sent 50,000 HTTP requests per second. These networked devices enable DDoS attack traffic to reach 1 Tbps. In 2017, the IoT platform will need to keep security in mind from the start, rather than planning afterwards. Today, simple use of telnet and factory default usernames and passwords can make botnets incredibly large. As the number of connected devices in the Internet of Things reaches billions in the next few years, and how devices are insecure, those botnets will only continue to increase. This security burden falls on three groups: manufacturers, network operators and corporate customers. While manufacturers must manufacture built-in, secure, resilient products, operators should detect and manage traffic to these devices to protect potential victims. Business customers need to be aware of the risks of infrastructure and assets and invest in protecting the IoT security against the threats that will occur in the next three to five years. PDoS threats against physical devices Next year there will be a Permanent Denial Of Service (PDoS) attack designed to destroy firmware for IoT devices and other hardware. One PDoS method is to remotely or physically manage the victim's hardware management interface. An attacker could exploit a vulnerability to replace a device's underlying software with a modified, corrupted, or defective firmware image. As a result, the device is destroyed and cannot be used until it is repaired or replaced. The “things†of the Internet of Things are particularly vulnerable to such attacks, as these “things†are often simple devices that lack inherent security measures. A clear understanding of the different firmware versions, binaries, chip-level software, and the technology used is required. Protecting the future security of the Internet of Things The long-term success of the Internet of Things is largely determined by the secure IoT platform. In 2017 and beyond, the Internet of Things will introduce new security measures, including device identification, automated supervision and availability. For example, with the advent of billions of non-traditional IT devices, the security value of permanent IP addresses will drop dramatically. Device fingerprinting will gradually become a common way to identify devices based on multiple attributes, instead of creating behaviors and credit records based on IP addresses. The requirements for automation in 2016 are extremely urgent, as is 2017. As automated attacks continue to increase, even security professionals cannot protect systems and devices from attacks. Only when the robot is against the robot can the organization effectively defend against the attack. Security regulation of the Internet of Things is essential (especially for employees responsible for equipment production and industrial control). In the logistics, public transportation, power and heating industries, all devices using IoT technology must be protected. Because of the integration of organizational services, and the increasing reliance on the Internet of Things, the pressure to maintain network availability will be greater. Any downtime can cause economic losses and affect productivity, but the far-reaching impact of the Internet of Things will be even more important. Only when the organization actively takes overall measures to enhance the security situation, the Internet of Things can be protected from the next wave of attacks and avoid disasters.
Advantage:
Unique guidepad geometry allows for excellent roundness and straightness, even in an interrupted cut condition.
Surface roughness is reduced obviously.
Reduced the machining time while maintaining a reliable process.
Step reamers are used to drill a hole in material with a
pilot hole. In order to improve machining efficiency, we usually use the process strategy with a solid carbide step
drill and step reamer reduces the processing time and produces a straight hole
with tight tolerances and an excellent surface finish.
Features
With 4, 6 or 8 flute
Multi-diameter
tool allowing for excellent hole size and concentricity between diameters.
Flexible in
order quantity:
Samples can be provided before mass production, and MOQ can
be discussed accordingly.
PRODUCT DETAIL:
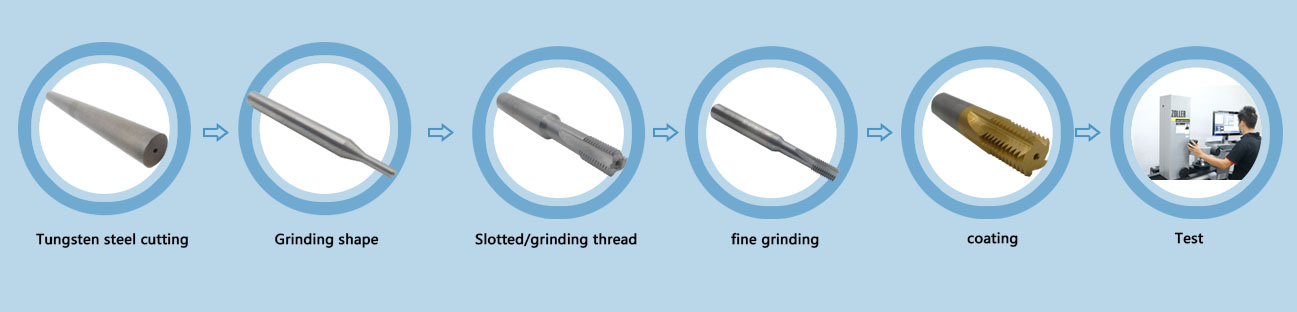
PRODUCTING PROGRESS:
PAYMENT AND DELIVERY:
PRODUCT EQUIPMENT :
+
ABOUT US :
We are specialize in manufacturing PCD diamond tools and Carbide tools. Our major product inclulde PCD Inserts , PCD Reamers , PCD End Mills, PCD Taps, Cabide Inserts,Carbide Drills, Carbide Reams, Taps etc.,
We also offered customized cutting tools per drawings, and provide package according to customer requirements. We manufacture a series range of cutting tools for machining of Cast iron, Aluminium alloy and Non-Ferros metal, it is widely used in all major sectors like Automobiles, Engineering, Aerospace, Aviation and 3C industry. Premium quality of raw material is used in the production and strict examination during processing with advanced equipment, so our client are satisfied with our reliable quality and on-time delivery.
Our best selling of cutting tools include PCD Inserts, PCD End Mill, PCD Ball Nose Mill, PCD Reamer, Carbide Taps, Carbide End Mill, Special Form Cutter and many more. For these years we have been made a large forward in the technologies of manufacturing cutting tools. With high quality on performance and price, our product sells well both on domestic and overseas market. And we will always focus on the quality and best service, to make long business relationship.
quanlity control:
We have dedicated team of quality control and precise equipment to keep good and stable performance for our products and processing services.
Adjustable Reamer Set,Hand Reamer,Adjustable Tapered Reamer,Carbide Tapered Reamer OPT Cutting Tools Co., Ltd. , https://www.optdiamondtoolss.com